1 - Scopo del documento
Lo scopo di questo documento è definire una configurazione funzione, per fornire la funzionalità di tunnel VPN IPSec utilizzando l'interfaccia del tunnel VTI tra i dispositivi Stormshield SNS e Fortinet Fortigate firewall
2 - Descrizione del laboratorio
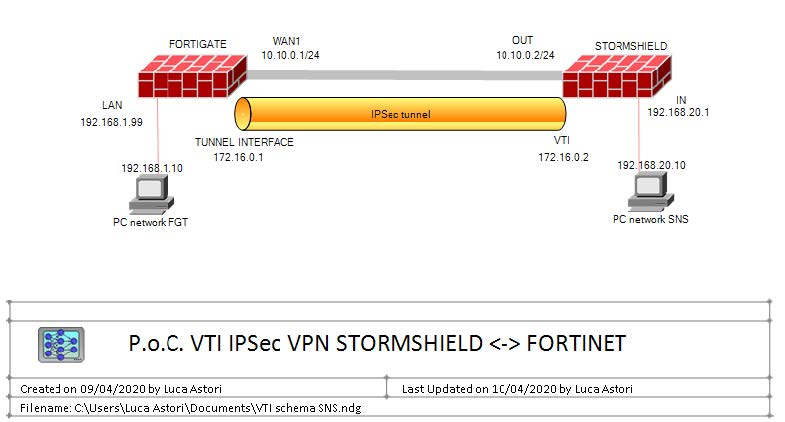
2.1 - Definizione dell'ambiete lato Stormshield
Stormshield INTERNAL network : 192.168.20.0 / 255.255.255.0
Stormshield INTERNAL IP Address : 192.168.20.1
Stormshiled INTERNAL workstation : 192.168.20.10
Stormshield OUT network : 10.10.0.0 / 255.255.255.0
Stormshield OUT IP Address : 10.10.0.2
Stormshield VTI Virtual Interface NAME: VPN_TO_FGT
Stormshield VTI Virtual Interface IP: 172.16.0.2 / 255.255.255.252
2.2 - Definizione dell'ambiete lato Fortinet
Fortinet INTERNAL network : 192.168.1.0/24
Fortinet INTERNAL IP Address : 192.168.1.99
Fortinet INTERNAL workstation : 192.168.1.10
Fortinet WAN1 network : 10.10.0.0 / 255.255.255.0
Fortinet WAN1 IP Address : 10.10.0.1
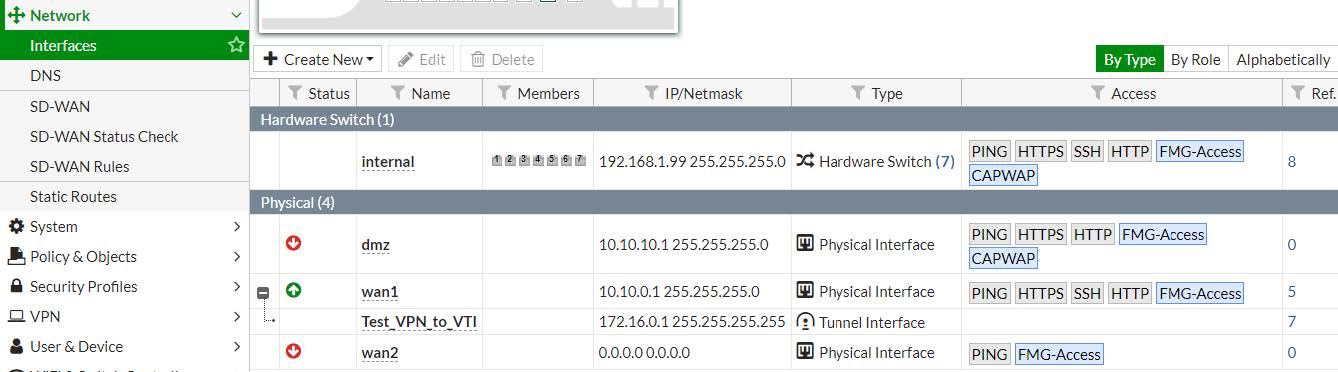
Fortinet TUNNEL Interface NAME : Test_VPN_to_VTI
Fortinet TUNNEL Interface IP Address : 172.16.0.1 / 255.255.255.255
3. - Configurazione
3.1 - Configurazione apparato Stormshield
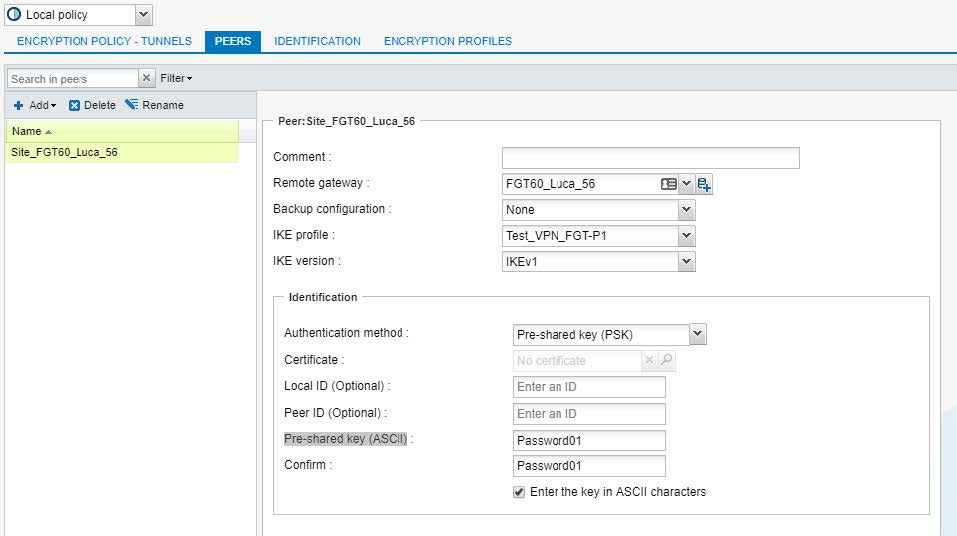
3.1.1 Creazione del "remote peer FGT"
Remote Gateway : FGT60_luca_56 = 10.10.0.1
IKE profile : Test_VPN_FGT-P1
IKE version: IKEv1
Identification: Pre-Shared key (PSK)
Pre-shared key (ASCII): Password01 (PAPA – alpha - sierra – sierra – wiskey – oscar – romeo – delta – ZERO – ONE)
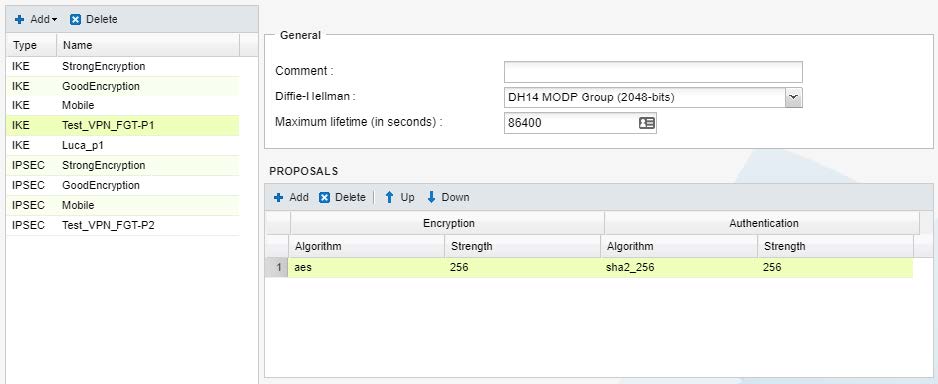
3.1.2 - Creazione dell'Encryption Profile
PHASE 1 IKE
nome Phase1 : Test_VPN_FGT-P1
Diffie-Hellman : DH14 MODP Group (2048-bits)
Maximum lifetime (in secondi) : 86400
Proposals :
Encryption: AES 256
Authentication: SHA2_256 256
PHASE 2 IPSEC
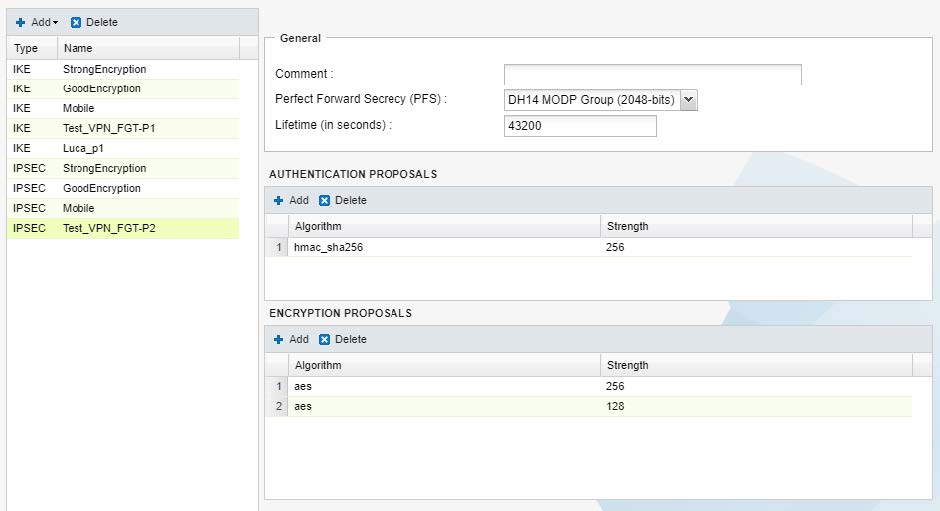
nome Phase2 : Test_VPN_FGT-P2
Perfect Forward Secrecy (PFS) : DH14 MODP Group (2048-bits)
Lifetime (in secondi) : 43200
Authentication Proposals: HMAC_SHA256 – 256
Encryption Proposals: AES 256 / AES 128
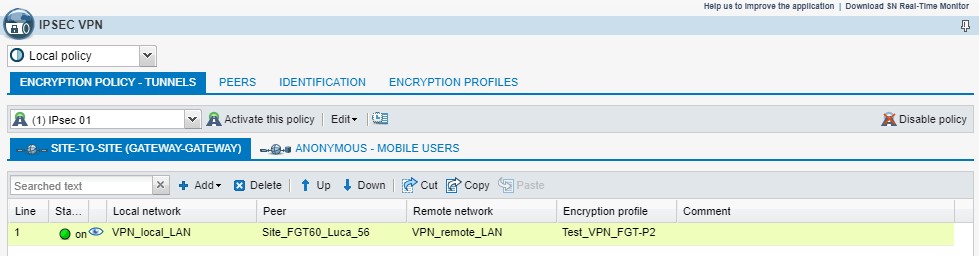
3.1.3 - Definizione della Configurazione Gateway-to-GatewayDefine a Site-to-Site (gw2gw) configuration
Local Network : VPN_local_LAN ( 192.168.20.0/255.255.255.0 )
Peer: Site_FGT60_luca_56 ( 10.10.0.1 )
Remote Network : VPN_remote_LAN ( 192.168.1.0/255.255.255.0 )
Encryption profile P2: Test_VPN_FGT-P2
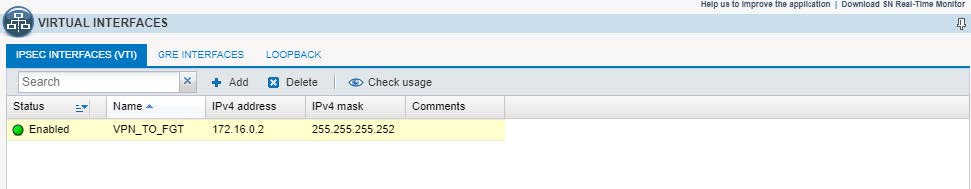
3.1.4 - Creazione dell'interfaccia IPSec (VTI)
Aggiungere una nuova interfaccia IPSec (VTI):
Nome: VPN_TO_FGT
IPv4 Address: 172.16.0.2
IPv4 mask: 255.255.255.252
3.1.5 - Configurazione della rotta statica
Destination network : VPN_remote_LAN
Address range : 192.168.1.0/24
Interface : VPN_TO_FGT
Gateway : FTG_VTI_IP (172.16.0.1)
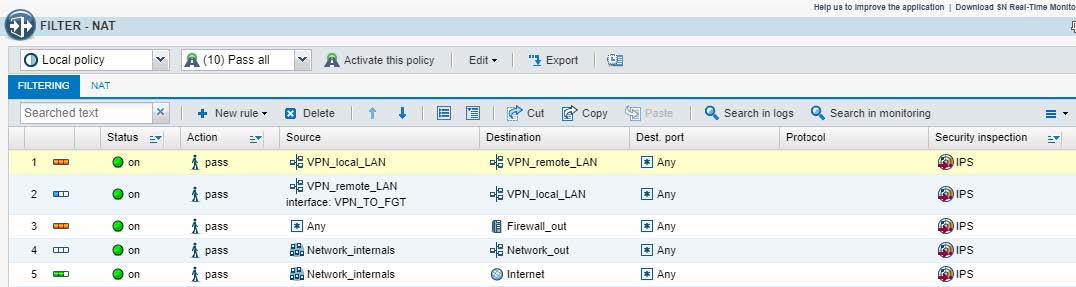
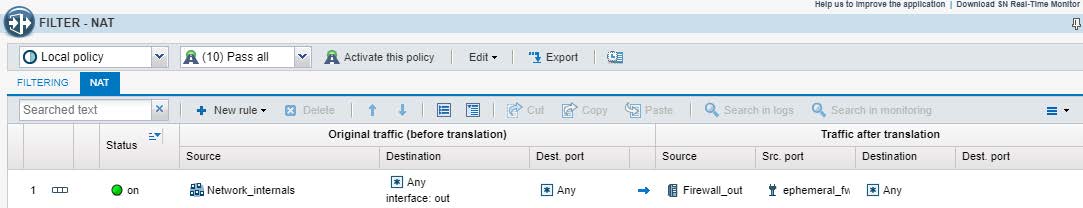
3.1.6 - Configurazione della policy di FILTRO e NAT
Action : PASS
Source: VPN_local_LAN (192.168.20.0/0)
Destination: VPN_remote_LAN (192.168.1.0/24)
Destination Port: ANY
Action : PASS
Source: VPN_remote_LAN (192.168.1.0/24)
Source Interface : VPN_TO_FGT
Destination: VPN_local_LAN (192.168.20.0/0)
Destination Port: ANY
3.2 - Configurazione apparato Fortinet
Gli apparati Fortinet normalmente creano la VPN IPSec sfruttando una “procedura guidata” che crea sia i peer remoti e anche le relative interfaccie tunnel.
Il suggerimento utile è quello di utilizzare questa procedura guidata e, successivamente al termine della stessa, trasformare la VPN in una "Custom VPN" o in alternativa è utilizzare la modalità di configurazione della CLI del FortiOS (ho inserito anche la configurazione via CLI a seguito dell rispettive parti via GUI).
Personalmente per questo documento ho utilizzato la procedura guidata del wizard che poi ho trasformato in una configurazione VPN Custom
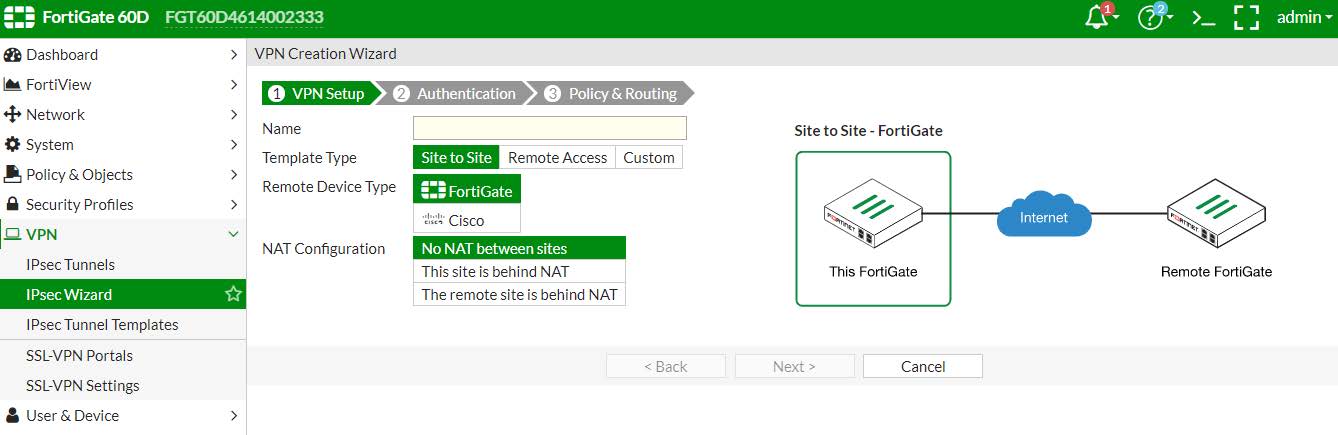
3.2.1 - Creazione del "remote peer" Stormshield
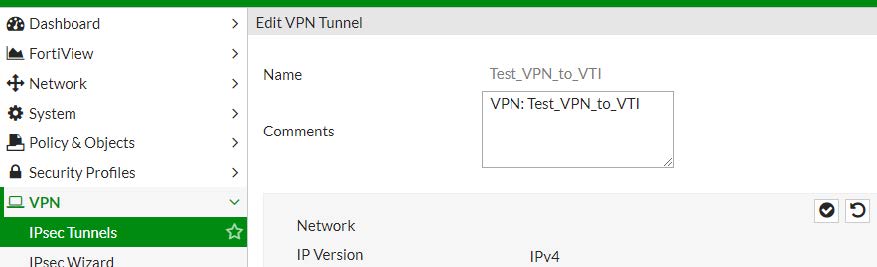
Nome : Test_VPN_to_VTI
Network
Remote Gateway : Static IP Address
IP Address : 10.10.0.2
Interface : WAN1
NAT Traversal : enable
Keepalice Frequency : 10
Dead Peer Detection : On Demand

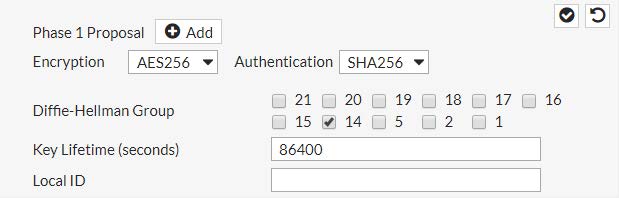
3.2.2 - Creazione dell'Encryption Profile
PHASE 1 Authentication / IKE
IKE Version: IKEv1
Authentication Method : Pre-shared key (PSK)
Pre-Shared key: Password01 (PAPA – alpha - sierra – sierra – wiskey – oscar – romeo – delta – ZERO – ONE)
Mode: MAIN Mode (ID protection)
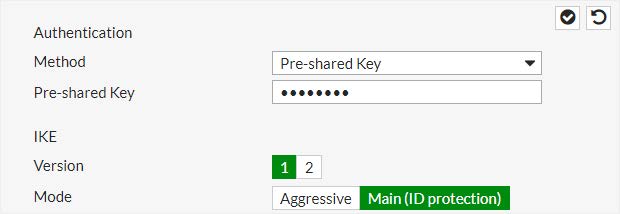
Diffie-Hellman Group : DH14 MODP Group (2048-bits)
Maximum lifetemi (in seconds) : 86400
Proposals :
Encryption: AES 256
Authentication: SHA2_256 256
PHASE 1 Authentication / IKE CLI config mode
config vpn ipsec phase1-interface
edit "Test_VPN_to_VTI"
set interface "wan1"
set peertype any
set proposal aes256-sha256
set comments "VPN: Test_VPN_to_VTI (Created by VPN wizard)"
set dhgrp 14
set remote-gw 10.10.0.2
set psksecret Password01
end
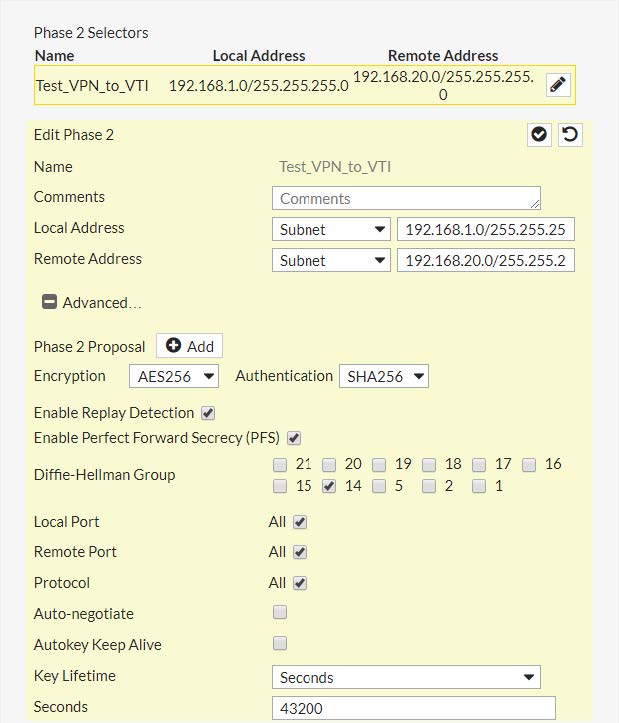
PHASE 2 IPSEC
Local Address: type SUBNET 192.168.1.0 / 255.255.255.0
Remote Address: type SUBNET 192.168.20.0 / 255.255.255.0
Phase 2 Proposal Encryption : AES256
Phase 2 Proposal Authentication : SHA256
Replay Detection : enable
Perfect Forward Secrecy (PFS) : Diffie-Hellman Group 14
Local Port : All
Remote Port : All
Protocol : All
Key Lifetime : seconds
Seconds : 43200
PHASE 2 IPSEC CLI config mode
config vpn ipsec phase2-interface
edit "Test_VPN_to_VTI"
set phase1name "Test_VPN_to_VTI"
set proposal aes256-sha256
set dhgrp 14
set src-subnet 192.168.1.0 255.255.255.0
set dst-subnet 192.168.20.0 255.255.255.0
next
end
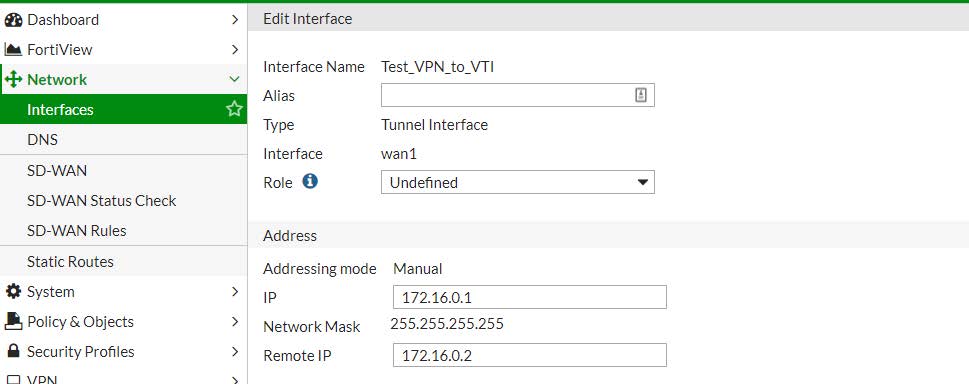
3.2.3 - Creazione della VPN Interface
Interface Name : Test_VPN_to_VTI
Type : Tunnel Interface
Interface (Bind) : WAN1
Addressing mode : Manual
IP Address Local: 172.16.0.1
Network Mask : 255.255.255.255
IP Address Remote (gateway) : 172.16.0.2
Creazione della VPN Interface in CLI config mode
config system interface
edit "Test_VPN_to_VTI"
set vdom "root"
set ip 172.16.0.1 255.255.255.255
set type tunnel
set remote-ip 172.16.0.2
set snmp-index 7
set interface "wan1"
next
end
3.2.4 - Creazione della rotta statica
Destination network : Test_VPN_to_VTI_remote_subnet
Address range : 192.168.20.0/24
Interface : Test_VPN_to_VTI
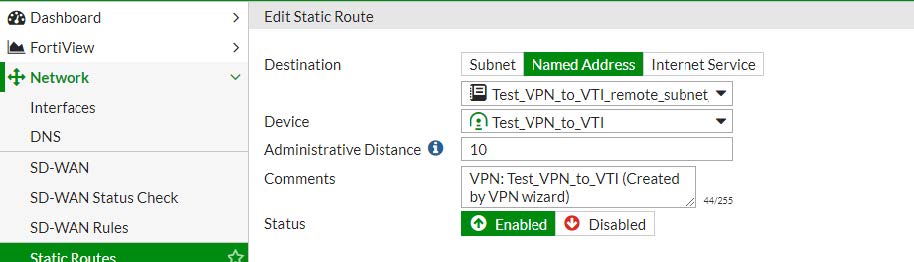
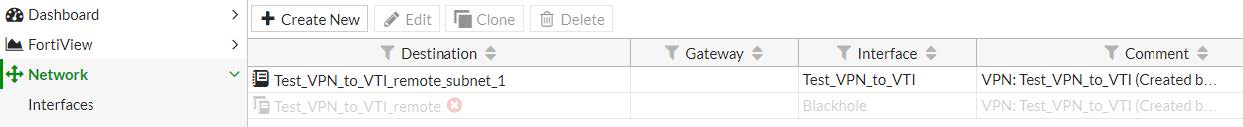
Creazione della Static Route in CLI config mode
config router static
edit 1
set device "Test_VPN_to_VTI"
set comment "VPN: Test_VPN_to_VTI (Created by VPN wizard)"
set dstaddr "Test_VPN_to_VTI_remote_subnet_1"
next
end
3.2.5 - Creazione delle Policy del traffico per la VPN
È necessario definire la politica di sicurezza / filtro bidirezionale tra “INTERNAL interface to Test_VPN_to_VTI” e Test_VPN_to_VTI interface to INTERNAL interface“
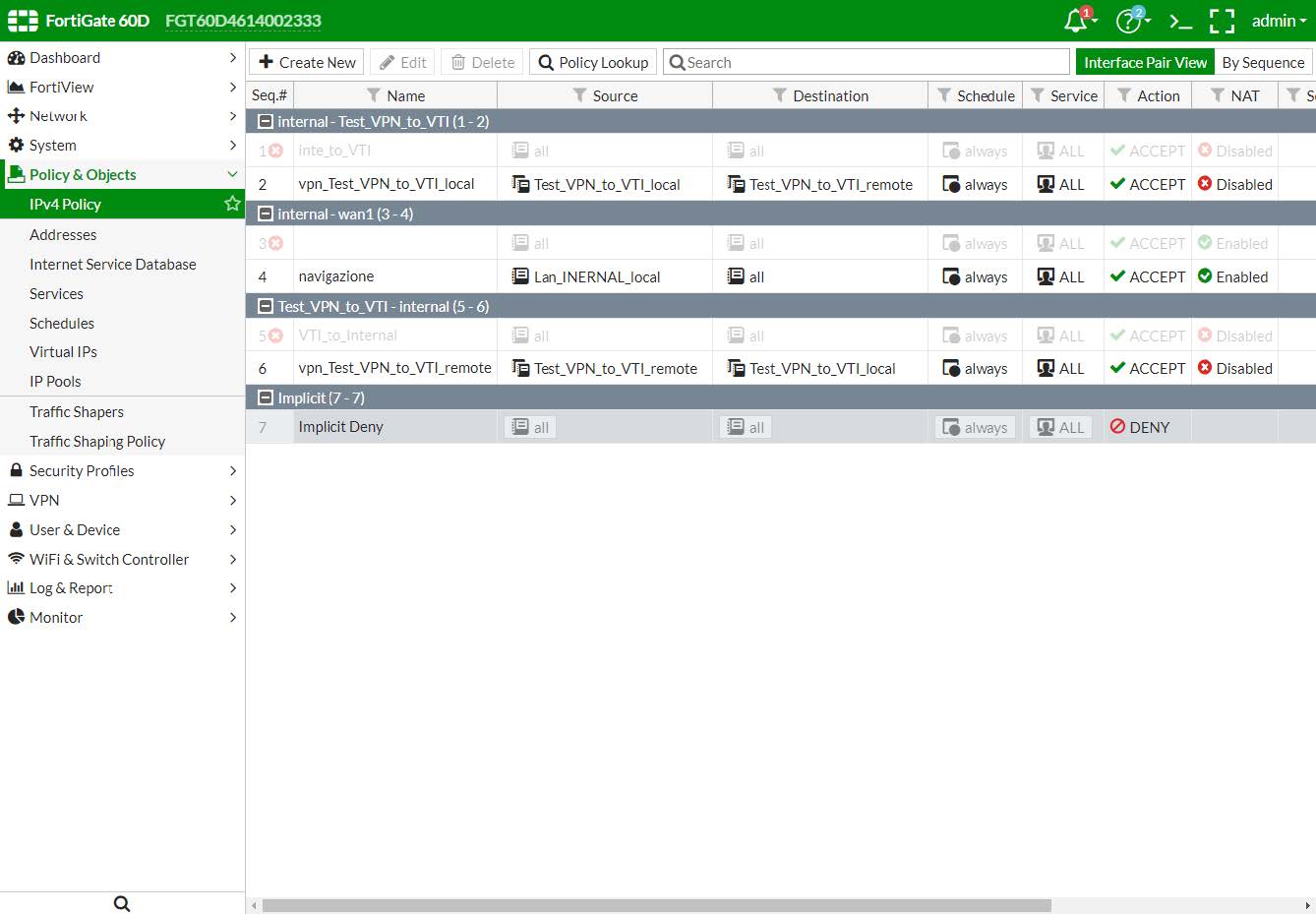
Policy: “INTERNAL interface to Test_VPN_to_VTI”
Name : vpn_Test_VPN_to_VTI_local
Incoming Interface : internal – (192.168.1.99)
Outgoing Interface : Test_VPN_to_VTI - (172.16.0.1)
Source : Test_VPN_to_VTI_local (192.168.1.0 255.255.255.0)
Destination : Test_VPN_to_VTI_remote (192.168.20.0 255.255.255.0)
Schedule : always
Service : ALL
Action : ACCEPT
Firewall / Network Options NAT : DISABLE
Creazione della policy in CLI config mode
config firewall policy
edit
set name "vpn_Test_VPN_to_VTI_local"
set srcintf "internal"
set dstintf "Test_VPN_to_VTI"
set srcaddr "Test_VPN_to_VTI_local"
set dstaddr "Test_VPN_to_VTI_remote"
set action accept
set schedule "always"
set service "ALL"
next
end
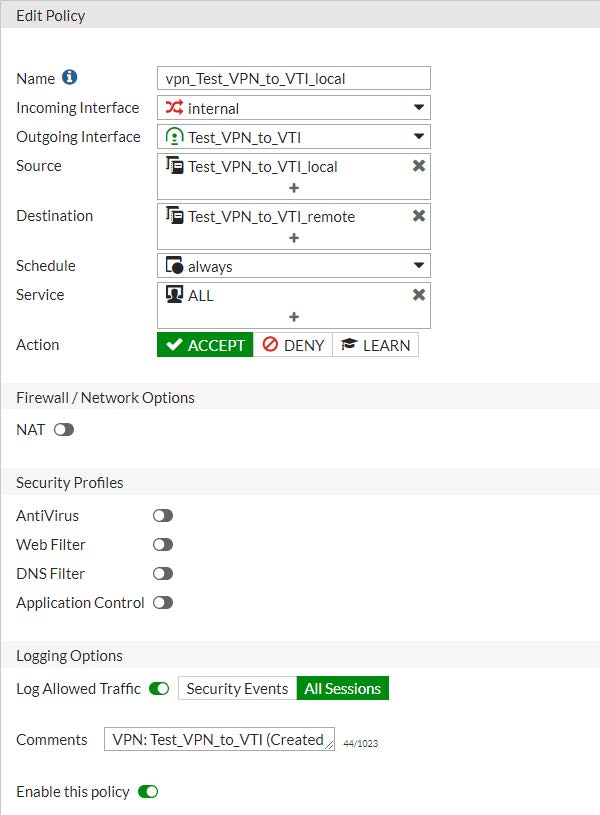
Policy: “Test_VPN_to_VTI to INTERNAL interface”
Name : vpn_Test_VPN_to_VTI_remote
Incoming Interface : Test_VPN_to_VTI (172.16.0.1)
Outgoing Interface : internal (192.168.1.99)
Source : Test_VPN_to_VTI_remote (192.168.20.0 255.255.255.0)
Destination : Test_VPN_to_VTI_local (192.168.1.0 255.255.255.0)
Schedule : always
Service : ALL
Action : ACCEPT
Firewall / Network Options NAT : DISABLE
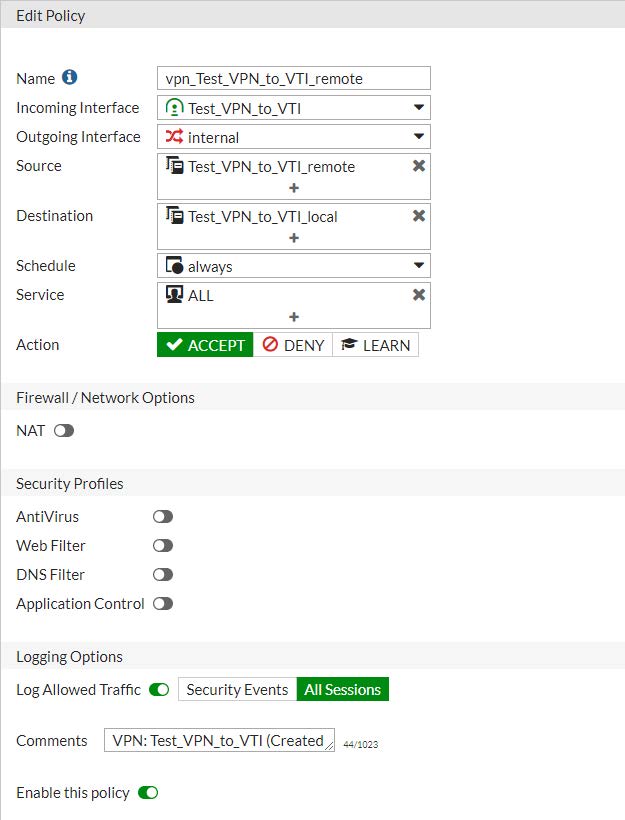
Creazione della policy in CLI config mode
config firewall policy
edit
set name "vpn_Test_VPN_to_VTI_remote"
set srcintf "Test_VPN_to_VTI"
set dstintf "internal"
set srcaddr "Test_VPN_to_VTI_remote"
set dstaddr "Test_VPN_to_VTI_local"
set action accept
set schedule "always"
set service "ALL"
next
end
4. - Test funzionamento VTI
4.1 - Situazione prima di inizializzazione del tunnel VPN
4.1.1 - Lato apparato Stormshield
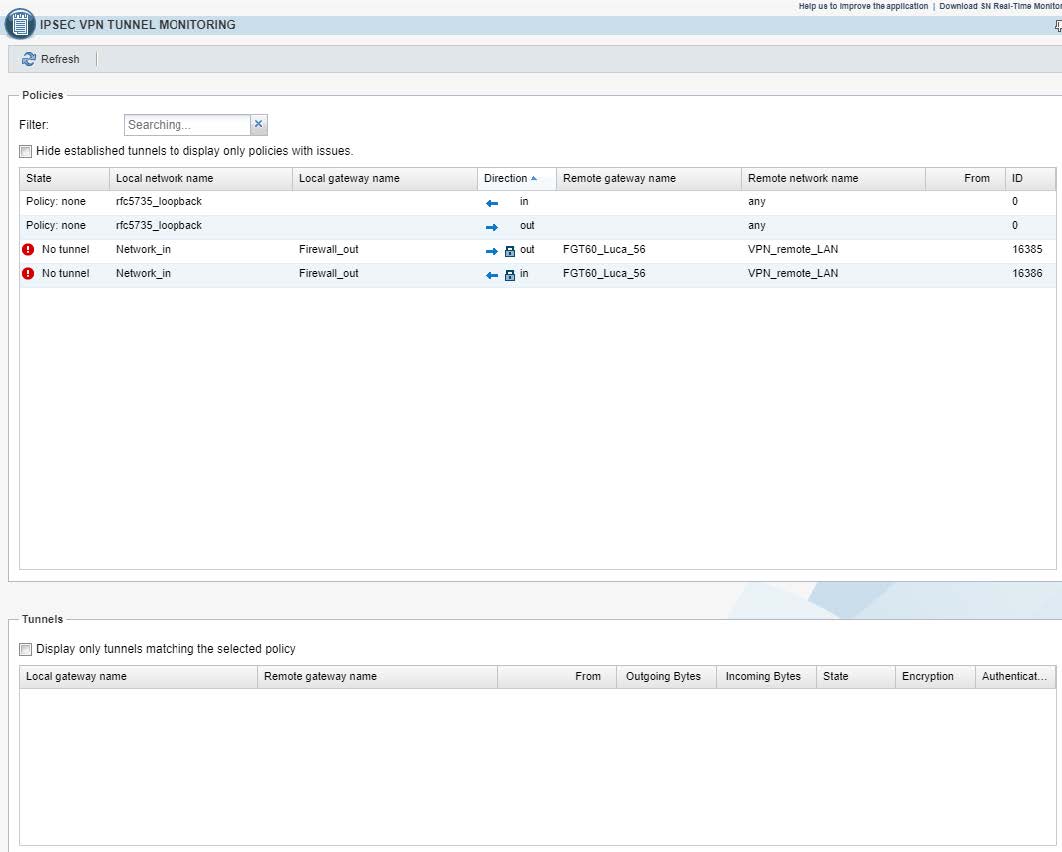
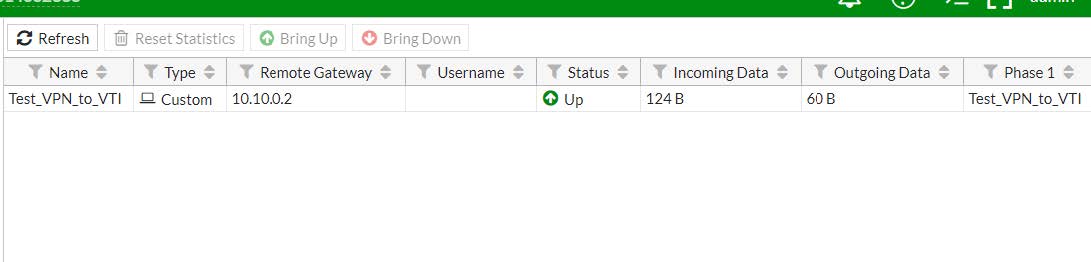
4.1.2 - Lato Fortinet
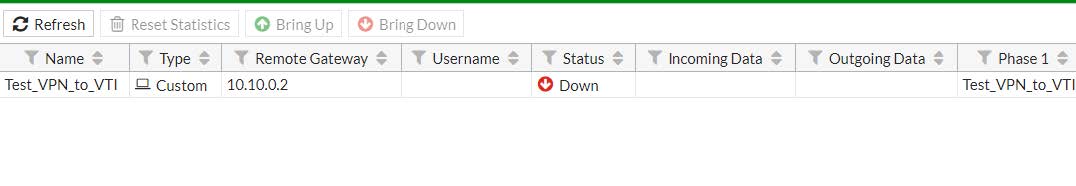
4.2 - Negoziazione della VPN IPSec VTI
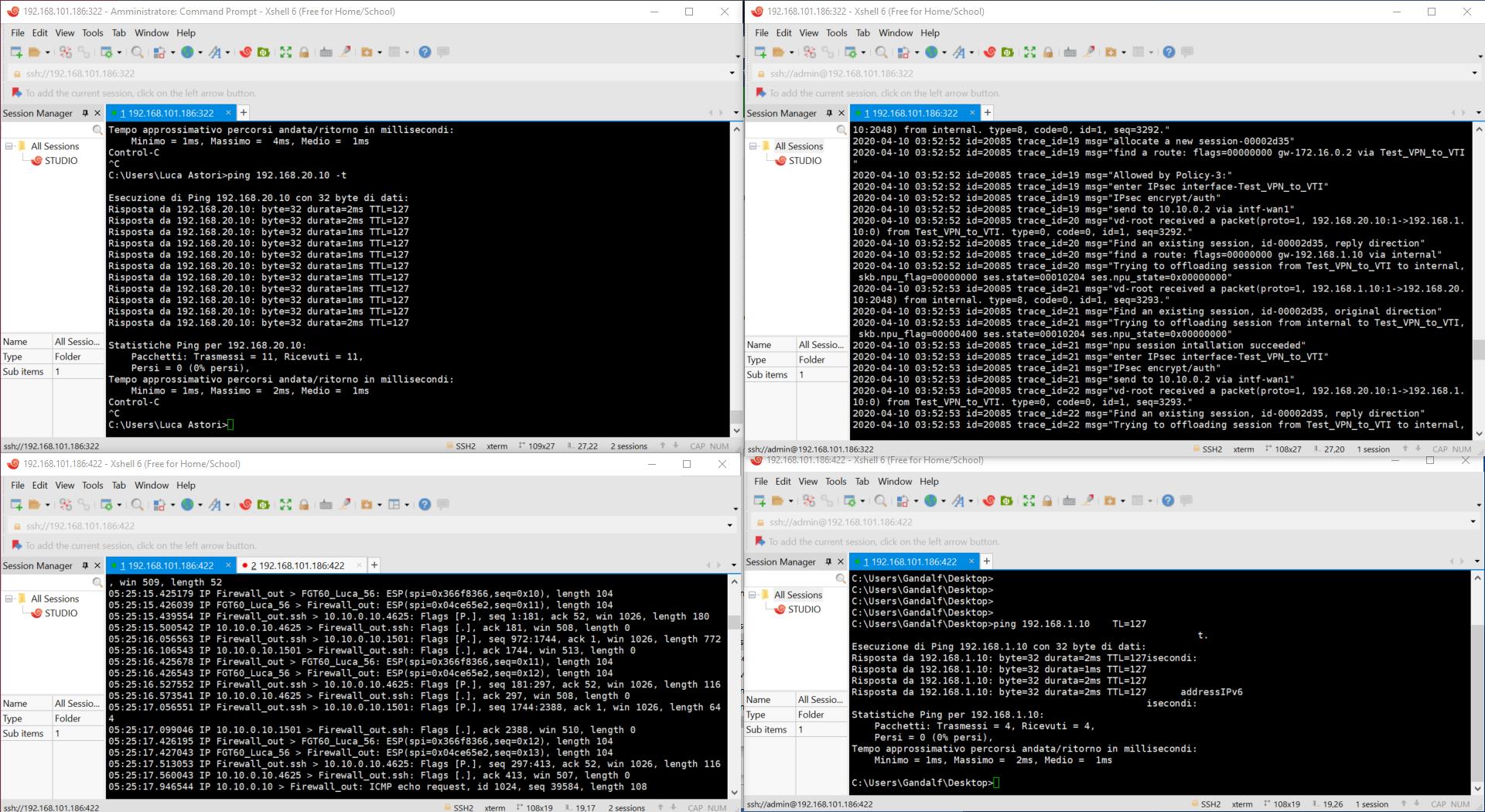
4.2.1 - dettaglio negoziazione lato Stormshield
2020-04-08 03:06:03: [10.10.0.1] DEBUG2: Checking remote conf "10.10.0.1[500]" 10.10.0.1[500].
2020-04-08 03:06:03: DEBUG2: enumrmconf: "10.10.0.1[500]" matches.
2020-04-08 03:06:03: DEBUG: ===
2020-04-08 03:06:03: INFO: respond new phase 1 negotiation: 10.10.0.2[500]<=>10.10.0.1[500]
2020-04-08 03:06:03: INFO: begin Identity Protection mode.
2020-04-08 03:06:03: DEBUG: begin.
-----
2020-04-08 03:06:03: INFO: received Vendor ID: RFC 3947
2020-04-08 03:06:03: [10.10.0.1] DEBUG2: Checking remote conf "10.10.0.1[500]" 10.10.0.1[500].
2020-04-08 03:06:03: DEBUG2: enumrmconf: "10.10.0.1[500]" matches.
2020-04-08 03:06:03: INFO: received Vendor ID: draft-ietf-ipsec-nat-t-ike-03
2020-04-08 03:06:03: INFO: received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
2020-04-08 03:06:03: [10.10.0.1] DEBUG2: Checking remote conf "10.10.0.1[500]" 10.10.0.1[500].
2020-04-08 03:06:03: DEBUG2: enumrmconf: "10.10.0.1[500]" matches.
2020-04-08 03:06:03: INFO: received Vendor ID: draft-ietf-ipsec-nat-t-ike-02
2020-04-08 03:06:03: [10.10.0.1] DEBUG2: Checking remote conf "10.10.0.1[500]" 10.10.0.1[500].
2020-04-08 03:06:03: DEBUG2: enumrmconf: "10.10.0.1[500]" matches.
2020-04-08 03:06:03: INFO: received Vendor ID: draft-ietf-ipsec-nat-t-ike-01
2020-04-08 03:06:03: INFO: received Vendor ID: draft-ietf-ipsec-nat-t-ike-00
2020-04-08 03:06:03: INFO: received Vendor ID: DPD
2020-04-08 03:06:03: DEBUG: remote supports DPD
2020-04-08 03:06:03: INFO: received Vendor ID: FRAGMENTATION
2020-04-08 03:06:03: INFO: received broken Microsoft ID: FRAGMENTATION
2020-04-08 03:06:03: DEBUG: received unknown Vendor ID
2020-04-08 03:06:03: DEBUG: 82990317 57a36082 c6a621de 000505a9
2020-04-08 03:06:03: [10.10.0.1] INFO: Selected NAT-T version: RFC 3947
2020-04-08 03:06:03: DEBUG: total SA len=56
-----
2020-04-08 03:06:03: DEBUG: type=Life Type, flag=0x8000, lorv=seconds
2020-04-08 03:06:03: DEBUG: type=Life Duration, flag=0x0000, lorv=4
2020-04-08 03:06:03: DEBUG: type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
2020-04-08 03:06:03: DEBUG: encryption(aes)
2020-04-08 03:06:03: DEBUG: type=Key Length, flag=0x8000, lorv=256
2020-04-08 03:06:03: DEBUG: type=Authentication Method, flag=0x8000, lorv=pre-shared key
2020-04-08 03:06:03: DEBUG: type=Hash Algorithm, flag=0x8000, lorv=SHA256
2020-04-08 03:06:03: DEBUG: hash(sha2_256)
2020-04-08 03:06:03: DEBUG: type=Group Description, flag=0x8000, lorv=2048-bit MODP group
2020-04-08 03:06:03: DEBUG: hmac(modp2048)
2020-04-08 03:06:03: DEBUG: pair 1:
2020-04-08 03:06:03: DEBUG: 0x290b02b0: next=0x0 tnext=0x0
2020-04-08 03:06:03: DEBUG: proposal #1: 1 transform
2020-04-08 03:06:03: DEBUG: type=Life Type, flag=0x8000, lorv=seconds
2020-04-08 03:06:03: DEBUG: type=Life Duration, flag=0x0000, lorv=4
2020-04-08 03:06:03: DEBUG: type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
2020-04-08 03:06:03: DEBUG: type=Key Length, flag=0x8000, lorv=256
2020-04-08 03:06:03: DEBUG: type=Authentication Method, flag=0x8000, lorv=pre-shared key
2020-04-08 03:06:03: DEBUG: type=Hash Algorithm, flag=0x8000, lorv=SHA256
2020-04-08 03:06:03: DEBUG: type=Group Description, flag=0x8000, lorv=2048-bit MODP group
2020-04-08 03:06:03: DEBUG: prop#=1, prot-id=ISAKMP, spi-size=0, #trns=1
2020-04-08 03:06:03: DEBUG: trns#=1, trns-id=IKE
2020-04-08 03:06:03: DEBUG: lifetime = 86400
2020-04-08 03:06:03: DEBUG: lifebyte = 0
2020-04-08 03:06:03: DEBUG: enctype = AES-CBC
2020-04-08 03:06:03: DEBUG: encklen = 256
2020-04-08 03:06:03: DEBUG: hashtype = SHA256
2020-04-08 03:06:03: DEBUG: authmethod = pre-shared key
2020-04-08 03:06:03: DEBUG: dh_group = 2048-bit MODP group
2020-04-08 03:06:03: [10.10.0.1] DEBUG2: Checking remote conf "10.10.0.1[500]" 10.10.0.1[500].
2020-04-08 03:06:03: DEBUG2: enumrmconf: "10.10.0.1[500]" matches.
2020-04-08 03:06:03: DEBUG2: checkisakmpsa: authmethod: 1 / 1
2020-04-08 03:06:03: DEBUG: an acceptable proposal found.
2020-04-08 03:06:03: DEBUG: hmac(modp2048)
2020-04-08 03:06:03: DEBUG: agreed on pre-shared key auth.
2020-04-08 03:06:03: DEBUG: new cookie: 7b7ab737d8e34458
-----
2020-04-08 03:06:19: DEBUG: getsainfo params: loc='192.168.20.0/24' rmt='192.168.1.0/24' peer='10.10.0.1' client='10.10.0.1' id=1
2020-04-08 03:06:19: DEBUG: evaluating sainfo: loc='192.168.20.0/24', rmt='192.168.1.0/24', peer='ANY', id=1
2020-04-08 03:06:19: DEBUG: check and compare ids : values matched (IPv4_subnet)
2020-04-08 03:06:19: DEBUG: cmpid target: '192.168.20.0/24'
2020-04-08 03:06:19: DEBUG: cmpid source: '192.168.20.0/24'
2020-04-08 03:06:19: DEBUG: check and compare ids : values matched (IPv4_subnet)
2020-04-08 03:06:19: DEBUG: cmpid target: '192.168.1.0/24'
2020-04-08 03:06:19: DEBUG: cmpid source: '192.168.1.0/24'
2020-04-08 03:06:19: DEBUG: selected sainfo: loc='192.168.20.0/24', rmt='192.168.1.0/24', peer='ANY', id=1
-----
2020-04-08 03:06:20: DEBUG: suitable SP found:192.168.20.0/24[0] 192.168.1.0/24[0] proto=any dir=out
2020-04-08 03:06:20: DEBUG: (proto_id=ESP spisize=4 spi=00000000 spi_p=00000000 encmode=Tunnel reqid=16386:16385)
2020-04-08 03:06:20: DEBUG: (trns_id=AES encklen=256 authtype=hmac-sha256)
2020-04-08 03:06:20: DEBUG: (trns_id=AES encklen=128 authtype=hmac-sha256)
2020-04-08 03:06:20: DEBUG: total SA len=52
-----
2020-04-08 03:06:20: DEBUG: type=Encryption Mode, flag=0x8000, lorv=Tunnel
2020-04-08 03:06:20: DEBUG: type=Key Length, flag=0x8000, lorv=256
2020-04-08 03:06:20: DEBUG: type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha256
2020-04-08 03:06:20: DEBUG: type=Group Description, flag=0x8000, lorv=14
2020-04-08 03:06:20: DEBUG: hmac(modp2048)
2020-04-08 03:06:20: DEBUG: pair 1:
2020-04-08 03:06:20: DEBUG: 0x290b0590: next=0x0 tnext=0x0
2020-04-08 03:06:20: DEBUG: proposal #1: 1 transform
2020-04-08 03:06:20: DEBUG: begin compare proposals.
2020-04-08 03:06:20: DEBUG: pair[1]: 0x290b0590
2020-04-08 03:06:20: DEBUG: 0x290b0590: next=0x0 tnext=0x0
2020-04-08 03:06:20: DEBUG: prop#=1 prot-id=ESP spi-size=4 #trns=1 trns#=1 trns-id=AES
2020-04-08 03:06:20: DEBUG: type=SA Life Type, flag=0x8000, lorv=seconds
2020-04-08 03:06:20: DEBUG: type=SA Life Duration, flag=0x8000, lorv=43200
2020-04-08 03:06:20: DEBUG: type=Encryption Mode, flag=0x8000, lorv=Tunnel
2020-04-08 03:06:20: DEBUG: type=Key Length, flag=0x8000, lorv=256
2020-04-08 03:06:20: DEBUG: type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha256
2020-04-08 03:06:20: DEBUG: type=Group Description, flag=0x8000, lorv=14
2020-04-08 03:06:20: DEBUG: peer's single bundle:
2020-04-08 03:06:20: DEBUG: (proto_id=ESP spisize=4 spi=335314c3 spi_p=00000000 encmode=Tunnel reqid=0:0)
2020-04-08 03:06:20: DEBUG: (trns_id=AES encklen=256 authtype=hmac-sha256)
2020-04-08 03:06:20: DEBUG: my single bundle:
2020-04-08 03:06:20: DEBUG: (proto_id=ESP spisize=4 spi=00000000 spi_p=00000000 encmode=Tunnel reqid=16386:16385)
2020-04-08 03:06:20: DEBUG: (trns_id=AES encklen=256 authtype=hmac-sha256)
2020-04-08 03:06:20: DEBUG: (trns_id=AES encklen=128 authtype=hmac-sha256)
2020-04-08 03:06:20: DEBUG: matched
2020-04-08 03:06:20: DEBUG: ===
2020-04-08 03:06:20: DEBUG: call pfkey_send_getspi
2020-04-08 03:06:20: DEBUG: pfkey GETSPI sent: ESP/Tunnel 10.10.0.1[500]->10.10.0.2[500]
-----
2020-04-08 03:06:20: DEBUG: transform #1 len=32
2020-04-08 03:06:20: DEBUG: type=SA Life Type, flag=0x8000, lorv=seconds
2020-04-08 03:06:20: DEBUG: type=SA Life Duration, flag=0x8000, lorv=43200
2020-04-08 03:06:20: DEBUG: life duration was in TLV.
2020-04-08 03:06:20: DEBUG: type=Encryption Mode, flag=0x8000, lorv=Tunnel
2020-04-08 03:06:20: DEBUG: type=Key Length, flag=0x8000, lorv=256
2020-04-08 03:06:20: DEBUG: type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha256
2020-04-08 03:06:20: DEBUG: type=Group Description, flag=0x8000, lorv=14
2020-04-08 03:06:20: DEBUG: hmac(modp2048)
2020-04-08 03:06:20: DEBUG: pair 1:
2020-04-08 03:06:20: DEBUG: 0x290b0590: next=0x0 tnext=0x0
2020-04-08 03:06:20: DEBUG: proposal #1: 1 transform
2020-04-08 03:06:20: DEBUG: hmac(modp2048)
-----
2020-04-0803:06:20: DEBUG: pfkey UPDATE succeeded: ESP/Tunnel 10.10.0.2[500]->10.10.0.1[500] spi=122441043(0x74c4d53)
2020-04-08 03:06:20: INFO: IPsec-SA established: ESP/Tunnel 10.10.0.2[500]->10.10.0.1[500] spi=122441043(0x74c4d53)
2020-04-08 03:06:20: INFO: IPsec-SA established: ESP/Tunnel 10.10.0.2[500]->10.10.0.1[500] spi=861082819(0x335314c3)
4.2.2 - Dettaglio negoziazione lato Fortinet
FGT60D4614002333 # diagnose debug application ike -1
FGT60D4614002333 # diagnose debug enable
FGT60D4614002333 # ike 0: comes 10.10.0.2:500->10.10.0.1:500,ifindex=5....
ike 0: IKEv1 exchange=Quick id=0299b1bc9a431d01/d7f27c7510623004:f4537960 len=476
ike 0:Test_VPN_to_VTI:0:0: responder received first quick-mode message
ike 0:Test_VPN_to_VTI:0:0: peer proposal is: peer:0:192.168.20.0-192.168.20.255:0, me:0:192.168.1.0-192.168.1.255:0
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: trying
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: matched phase2
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: autokey
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: my proposal:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: proposal id = 1:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: protocol id = IPSEC_ESP:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: PFS DH group = 14
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: trans_id = ESP_AES_CBC (key_len = 256)
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: encapsulation = ENCAPSULATION_MODE_TUNNEL
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: type = AUTH_ALG, val=SHA2_256
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: incoming proposal:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: proposal id = 1:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: protocol id = IPSEC_ESP:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: PFS DH group = 14
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: trans_id = ESP_AES_CBC (key_len = 256)
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: encapsulation = ENCAPSULATION_MODE_TUNNEL
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: type = AUTH_ALG, val=SHA2_256
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: trans_id = ESP_AES_CBC (key_len = 128)
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: encapsulation = ENCAPSULATION_MODE_TUNNEL
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: type = AUTH_ALG, val=SHA2_256
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: negotiation result
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: proposal id = 1:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: protocol id = IPSEC_ESP:
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: PFS DH group = 14
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: trans_id = ESP_AES_CBC (key_len = 256)
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: encapsulation = ENCAPSULATION_MODE_TUNNEL
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: type = AUTH_ALG, val=SHA2_256
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: set pfs=MODP2048
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: using tunnel mode.
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: replay protection enabled
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: SA life soft seconds=42933.
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: SA life hard seconds=43200.
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: IPsec SA selectors #src=1 #dst=1
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: src 0 7 0:192.168.1.0-192.168.1.255:0
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: dst 0 7 0:192.168.20.0-192.168.20.255:0
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: add IPsec SA: SPIs=366f8366/04ce65e2
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: IPsec SA dec spi 366f8366
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: IPsec SA enc spi 04ce65e2
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: added IPsec SA: SPIs=366f8366/04ce65e2
ike 0:Test_VPN_to_VTI:0:Test_VPN_to_VTI:0: sending SNMP tunnel UP trap
FGT60D4614002333 # diagnose debug flow filter proto 1
FGT60D4614002333 # diagnose debug flow show
FGT60D4614002333 # diagnose debug console timestamp enable
FGT60D4614002333 # diagnose debug flow trace start 999
FGT60D4614002333 # diagnose debug enable
2020-04-10 03:52:52 id=20085 trace_id=19 msg="allocate a new session-00002d35"
2020-04-10 03:52:52 id=20085 trace_id=19 msg="find a route: flags=00000000 gw-172.16.0.2 via Test_VPN_to_VTI"
2020-04-10 03:52:52 id=20085 trace_id=19 msg="Allowed by Policy-3:"
2020-04-10 03:52:52 id=20085 trace_id=19 msg="enter IPsec interface-Test_VPN_to_VTI"
2020-04-10 03:52:52 id=20085 trace_id=19 msg="IPsec encrypt/auth"
2020-04-10 03:52:52 id=20085 trace_id=19 msg="send to 10.10.0.2 via intf-wan1"
2020-04-10 03:52:52 id=20085 trace_id=20 msg="vd-root received a packet(proto=1, 192.168.20.10:1->192.168.1.10:0) from Test_VPN_to_VTI. type=0, code=0, id=1, seq=3292."
2020-04-10 03:52:52 id=20085 trace_id=20 msg="Find an existing session, id-00002d35, reply direction"
2020-04-10 03:52:52 id=20085 trace_id=20 msg="find a route: flags=00000000 gw-192.168.1.10 via internal"
2020-04-10 03:52:52 id=20085 trace_id=20 msg="Trying to offloading session from Test_VPN_to_VTI to internal, skb.npu_flag=00000000 ses.state=00010204 ses.npu_state=0x00000000"
2020-04-10 03:52:53 id=20085 trace_id=21 msg="vd-root received a packet(proto=1, 192.168.1.10:1->192.168.20.10:2048) from internal. type=8, code=0, id=1, seq=3293."
2020-04-10 03:52:53 id=20085 trace_id=21 msg="Find an existing session, id-00002d35, original direction"
2020-04-10 03:52:53 id=20085 trace_id=21 msg="Trying to offloading session from internal to Test_VPN_to_VTI, skb.npu_flag=00000400 ses.state=00010204 ses.npu_state=0x00000000"
2020-04-10 03:52:53 id=20085 trace_id=21 msg="npu session intallation succeeded"
2020-04-10 03:52:53 id=20085 trace_id=21 msg="enter IPsec interface-Test_VPN_to_VTI"
2020-04-10 03:52:53 id=20085 trace_id=21 msg="IPsec encrypt/auth"
2020-04-10 03:52:53 id=20085 trace_id=21 msg="send to 10.10.0.2 via intf-wan1"
4.3 - Situazione a seguito completamento della negoziazione VPN
4.3.1 - Lato Stormshield
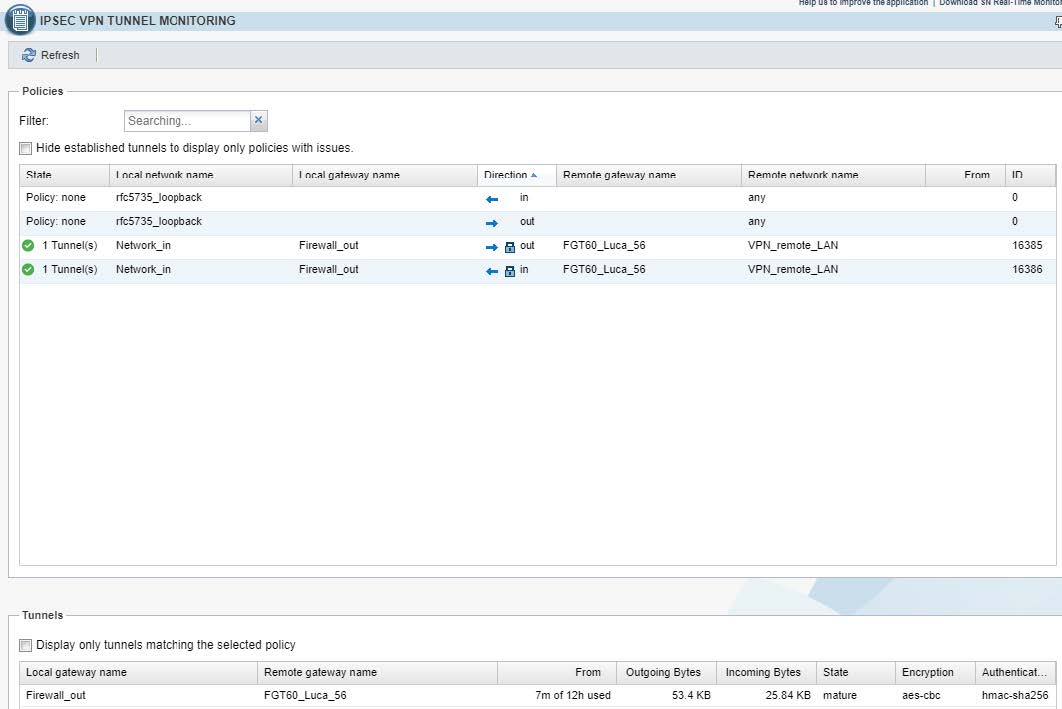
4.3.2 - Lato Fortinet